IT assurance reporting increasingly popular, but what exactly is it?
By Marjolein Veenstra (scheme manager information security at Kiwa) and Jouke Albeda (managing director at risk and compliance expert 3angles)
The growing number of requirements for information and IT security instigates more and more organizations to demonstrate that they have done everything within reach to comply with applicable laws and regulations and that they work according to recognized quality and information security standards. In addition to certification in accordance with the ISO 27001 standard for information security, an increasing number of organizations is opting for IT assurance reports such as ISAE 3402 and SOC 2. But what exactly are these IT assurance reports? And how do they compare to ISO 27001?
The ISO 27001 quality standard focuses on the implementation and maintenance of the information security management system and the design and implementation of control measures, based, among other things, on best practices. Assurance reports (such as ISAE 3402 and SOC 2) focus on providing a degree of certainty with regard to the effective operation or implementation of specific control measures. The importance of both the implementation of best practices and the management system and the effective functioning of controls has become increasingly clear to companies and their customers.
Origins in accountancy
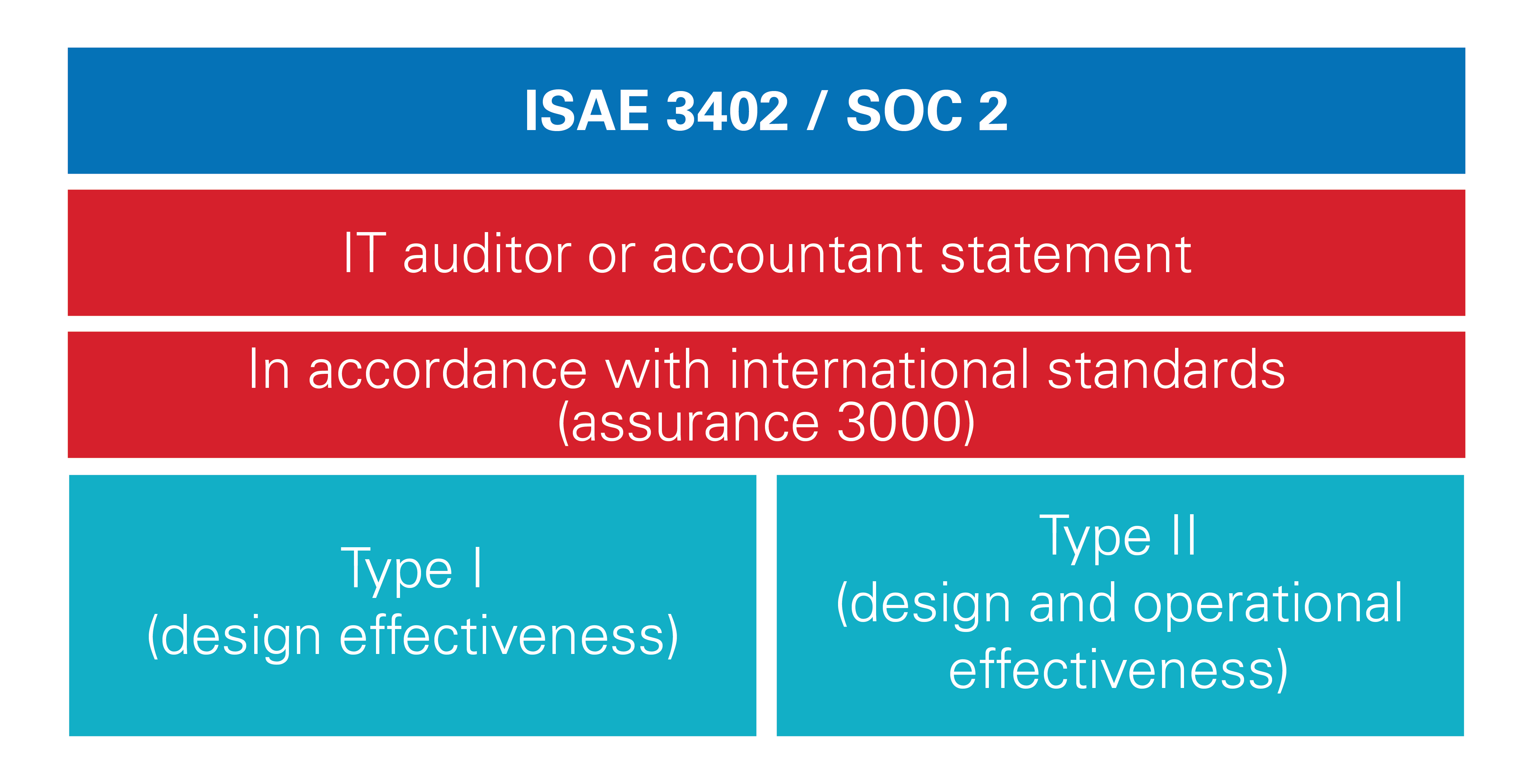
The origin of the assurance report ISAE3402 and SOC 2 lies in the accounting world. To gain certainty about the reliability of financial information, the reliability of the systems which process this information must be mapped out. There is more and more software that can have an impact on financial data processing or the continuity of a company. To manage risks, solutions are increasingly being sought to obtain certainty about processes that have been outsourced. The accountant must also assess and possibly test the risks of outsourced services for the annual audit.
Best practices
The ISO standards for information security have been developed by renowned organizations that together have come up with a set of best practices. Paramount to this is a management system that supports organizations in the continuous improvement of information security with the well-known 'Plan-do-check-act' (PDCA) cycle. The use of best practices, the ability to continuously improve and the assurance that controls are in place and operating effectively are important to customers of IT service providers. Due to the difference in origin, the supervisor also differs: for ISO 27001 this is the Dutch Accreditation Council (Raad voor Accreditatie, RvA) and for assurance reports this is NOREA.
Substantive differences
There are many similarities between ISO 27001, ISAE 3402 and SOC 2. In both cases, the implementation of control measures and the operation of business processes are examined. But there are also big differences. An ISAE 3402 and SOC 2 audit focuses on providing a degree of assurance about the implementation (also referred to as type I) and/or the effective operation over a period of usually at least six months (also referred to as type II ) in the recent past. For this, statistical sampling is being used: a sample is taken from a population of, for example, registrations over the reporting period. An ISO 27001 audit looks less far into history and focuses on the present and the future. As a result, you often see ISO 27001 certification first and then an assurance report. Another important difference is that the qualifications for an ISO auditor are different than for a RE IT auditor (an IT auditor authorized to perform assurance audits).
Differences in audit approach
The way in which an audit is approached also has both differences and similarities. In both cases it is necessary to establish a clear scope and to coordinate which control measures are tested. The auditor will assess, both in an ISO 27001 and an ISAE 3402/SOC 2 audit, whether he considers the control measures to be tested applicable to the organization (in an ISO 27001 audit, specific attention is paid to the Statement of Applicability and in the case of an assurance report to the scope). During the audit, an ISO 27001 auditor will not collect evidence, but will review evidence and be guided through the ISMS and business processes. In an assurance audit, the auditor will collect evidence to form a file.
Samples
The way samples are selected also works differently: in an ISO 27001 audit, a sample is carried out during the audit and registrations and documents are examined. In an assurance audit, samples are drawn from a population according to a schedule that the audit firm uses to achieve a certain level of assurance. The amount of work involved and the lead time of an assurance audit is therefore often higher than with an ISO 27001 audit. At the end of the audit, a quality review is performed on the file in both cases.
Differences in demand
Both assurance-related audits and ISO 27001 audits can be important to an organization for various reasons. One of the main reasons is customer-driven, but the intrinsic needs of the organization are also increasing. When asking for an ISO 27001 certificate, the customer is looking for confirmation that there is a working management system that reduces risks to an acceptable level, that an organization has established its business processes in accordance with best practices and that it has the ability to continuously improve. An ISAE 3402/SOC 2 audit is driven by the accountant of the end-user seeking assurance that risks have been mitigated over a specific time period. The assurance report is used by the accountant as part of the audit of the annual accounts, so that he does not have to visit the service provider.
| ISO-Audit | ISAE 3402/SOC 2 | |
| Origins | Best Practices | Annual account audit |
| Auditor education | ISO | RE |
| Supervisor | RvA | NOREA |
| Request documents | No | Yes |
| Internal quality review | Yes | Yes |
| Control measure review | Yes | Yes |
| International recognition | Yes | Yes |
More information
Although ISO 27001 certification and ISAE 3402 and SOC 2 reports serve different purposes, there are so many similarities that Kiwa can think along with partner 3angles about achieving efficiency benefits when performing both audits. If you would like to know more about this, please contact us and send an email to nl.cybersecurity@kiwa.com.
