In 7 steps towards ISO 27001:2022

ISO 27001, the globally recognized standard for information security, underwent an update. The revised standard ISO 27001:2022 was published on 25 October 2022 and contains several technical corrections and a completely revised Annex A. A transition period of three years applies to the renewed standard, which means that certified organizations must have transferred by November 1st 2025, at the latest. Below are the seven necessary steps before executing the transition audit.
Step 1: Gap analysis
This step involves identifying the effects of the new standard. What is the impact? What elements of the management system does the revised standard affect? This includes the Statement of Applicability, risk analysis, internal audit, policy documents, (operational) procedures, guidelines, etc.
Step 2: Action plan
Actions will arise from the gap analysis. Create a plan that specifies how the actions will be implemented, who will execute them and when.
Step 3: Adjust risk analysis and treatment plan
The existing risk analysis specifies the measures taken to mitigate risks. These measures must be compared with Annex A to verify that no necessary measures have been forgotten. Since Annex A has been revised, the risk analysis must be performed and adjusted again.
Step 4: Adjust control measures
Eleven new controls have been added and various controls have been merged. Use a risk analysis to identify which controls apply and how they are/will be implemented.
Step 5: Adjust the Statement of Applicability
Revise the Statement of Applicability and incorporate the new set of controls.
Step 6: Conduct internal audit
Perform an (additional) internal audit. This must include at least:
- The adjusted risk analysis and the corresponding treatment plan
- The new and modified (merged) controlsfrom Annex A.
Step 7: Management review
Perform an (additional) management review. Since elements such as risk analysis, risk treatment plan and internal audit have been adjusted, these must be reviewed by management.
When can you make the transition to ISO 27001:2022?
In response to an update from the International Accreditation Forum:
- During recertification
In contrast to earlier reports, half a day of extra audit time will be charged. - During the annual follow-up or control audit
Kiwa will schedule and charge an extra day for this, as well as the cost of a new certificate.
If you want to make the transition, please notify us as soon as possible (preferably four months before the audit). Our planning department will make additional arrangements with you.
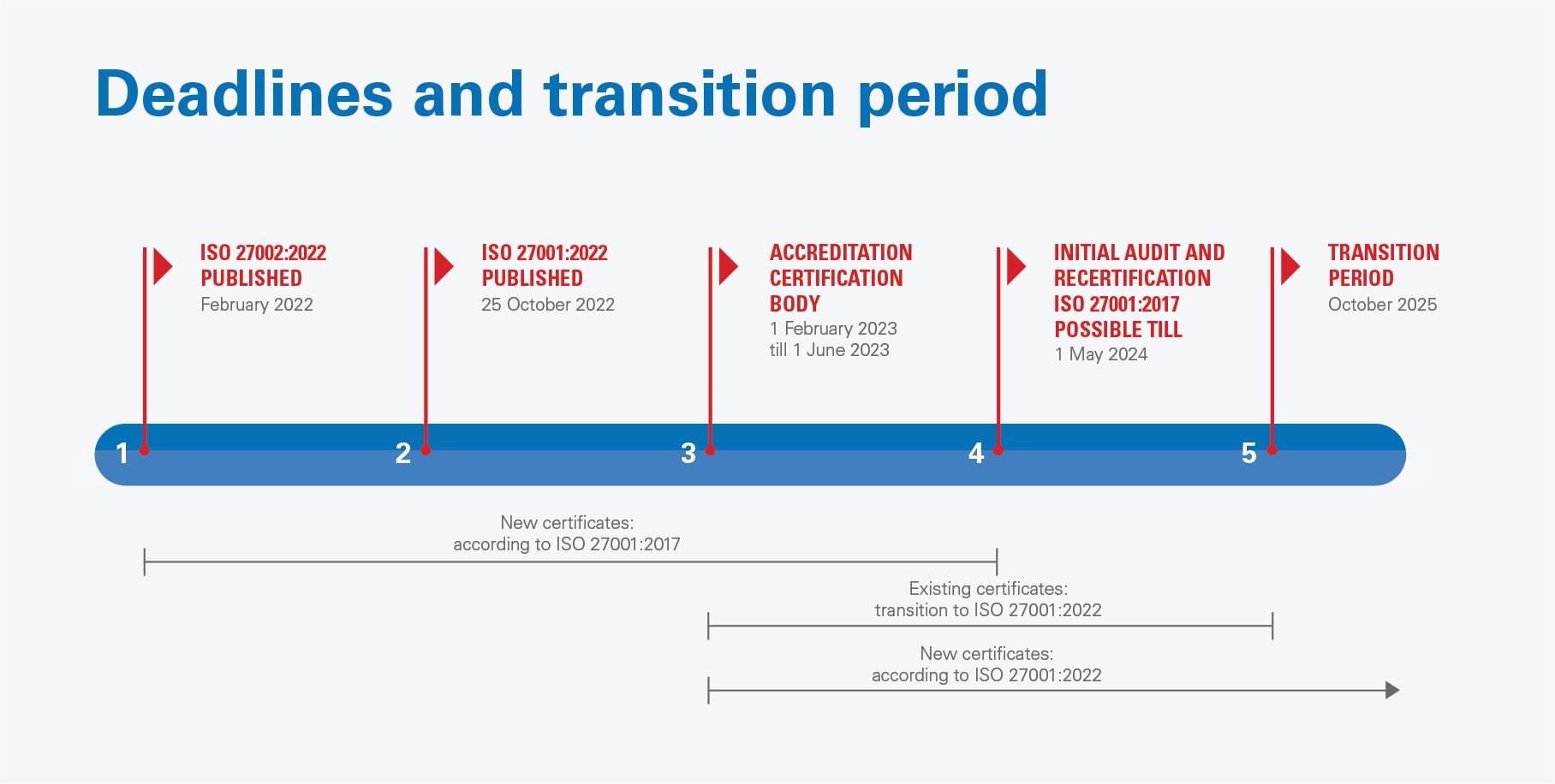
What does the transition period look like?
When a standard is revised, a transition period is established. A transition period of three years is maintained for this update. Within this period, all certificate holders must comply with ISO 27001:2022. Below is the timeline for this transition period:
Download the timeline ISO 27001:2022 (version 28 June 2024).
In short:
- From 1 March 2023, Kiwa can conduct audits according to ISO 27001:2022
- The transition period for ISO 27001:2022 ends on November 1st 2025
- Until May 1st 2024 Kiwa can conduct initial audits and recertifications against ISO 27001:2017, after this date these types of audits will be conducted against ISO 27001:2022
- Follow-up or surveillance audits can be conducted against ISO 27001:2017 until November 1st 2025
Contact
The new ISO 27001:2022
- One revised ISO 27001, three different versions
- Five questions about the revised ISO 27001:2022
- 1 Feb 2023: Kiwa officially accredited
- 9 Dec 2022: Transition to new version ISO 27001:2022
- 27 Okt 2022: ISO 27001 standard for information security revised
- 2 Aug 2022: The most important changes to the revised ISO 27001 and ISO 27002